7 Types of hacker
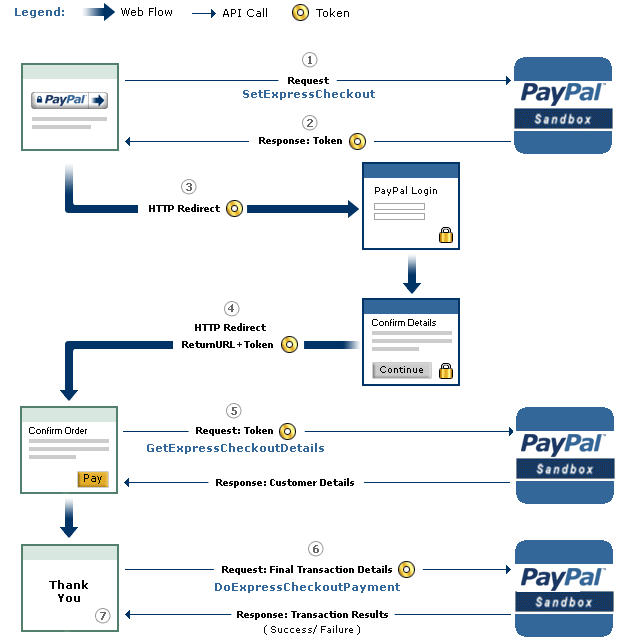
1-Script Kiddies-They are just download overused software & watch youtube video on how to use it. Script kiddies don't care about hacking.
2-White Hat-They are the good guys of the hacker world. They also known as Ethical Hacker.
3-Black Hat-They finds bank or other companies with weak security and steal money or credit card information. They also known as cracker. They are dangerous because they are illegal to gain unauthorized access.
4-Gray Hat-They don't steal money or information sometimes they deface a website or they don't help people for good.
5-Green Hat-These are the hacker "noobz" but unlike Script Kiddies.They care about Hacking and strive to become full-blown hacker.
6-Red Hat-These are the vigilantes of the hacker world. They are like White Hats in that they halt Black Hats but these folks are downright SCARY to those who have ever tried so much as penetrest.
7-Blue Hat-If a Script Kiddy took revenge he/she might become a Blue Hat.Most Blue Hats are noobz.They have no desire to learn.
1-Script Kiddies-They are just download overused software & watch youtube video on how to use it. Script kiddies don't care about hacking.
2-White Hat-They are the good guys of the hacker world. They also known as Ethical Hacker.
3-Black Hat-They finds bank or other companies with weak security and steal money or credit card information. They also known as cracker. They are dangerous because they are illegal to gain unauthorized access.
4-Gray Hat-They don't steal money or information sometimes they deface a website or they don't help people for good.
5-Green Hat-These are the hacker "noobz" but unlike Script Kiddies.They care about Hacking and strive to become full-blown hacker.
6-Red Hat-These are the vigilantes of the hacker world. They are like White Hats in that they halt Black Hats but these folks are downright SCARY to those who have ever tried so much as penetrest.
7-Blue Hat-If a Script Kiddy took revenge he/she might become a Blue Hat.Most Blue Hats are noobz.They have no desire to learn.
Read more
- Wifi Hacking App
- Servicio Hacker
- Phishing Hacking
- Curso De Hacking Etico
- Hacking With Arduino
- Hacking Youtube
- Hacking Growth Sean Ellis
- Growth Hacking Tools
- Hacking 2018
- Wordpress Hacking
- Hacking Con Buscadores Pdf
- Que Es Hacking Etico
- Reddit Hacking
- Hacking Mifare
- Hacker Profesional
- Paginas De Hackers